How Do I Use My Raspberry Pi 4 As A Firewall?
Are you looking for a cost-effective way to secure your network using a Raspberry Pi 4? You’re in the right place. Setting up your Raspberry Pi 4 as a firewall can significantly enhance your network's security while giving you complete control over your data flow. This guide will walk you through everything you need to know about transforming your Raspberry Pi 4 into a powerful firewall.
Firewalls are essential tools for protecting your network from unauthorized access and cyber threats. By leveraging the versatility and affordability of the Raspberry Pi 4, you can build a highly capable firewall that meets your specific needs. Whether you're a home user or managing a small business, this setup can offer robust security solutions.
In this comprehensive guide, we’ll cover everything from the basics of firewalls to step-by-step instructions for configuring your Raspberry Pi 4. We’ll also explore the best software options, troubleshooting tips, and additional security measures to ensure your network remains safe and secure.
Table of Contents
- Introduction to Firewalls
- Raspberry Pi 4 Overview
- Why Use Raspberry Pi as a Firewall?
- Software Options for Raspberry Pi Firewall
- Step-by-Step Guide to Setting Up a Firewall
- Network Configuration
- Advanced Security Settings
- Troubleshooting Tips
- Additional Security Measures
- Conclusion
Introduction to Firewalls
Firewalls act as a barrier between your internal network and the external world, filtering incoming and outgoing traffic based on predefined security rules. They play a crucial role in protecting your network from malicious attacks, unauthorized access, and data breaches.
There are several types of firewalls, including:
- Packet-filtering firewalls
- Stateful inspection firewalls
- Next-generation firewalls
- Proxy firewalls
Understanding the basics of firewalls is essential before diving into the setup process. A well-configured firewall can significantly enhance your network's security posture, ensuring that only legitimate traffic is allowed to pass through.
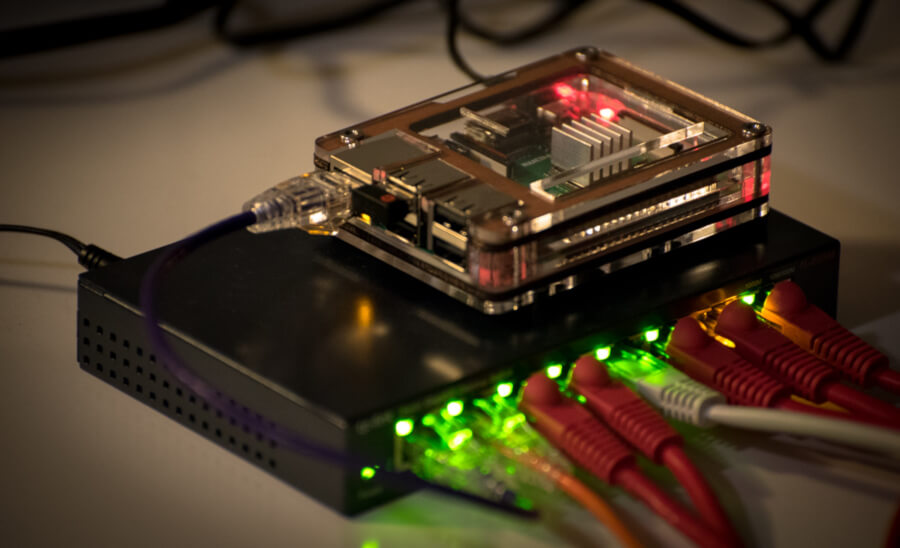
Raspberry Pi 4 Overview
The Raspberry Pi 4 is a powerful single-board computer that offers excellent performance for its price. Equipped with a quad-core processor, up to 8GB of RAM, and multiple connectivity options, it is an ideal platform for running network security applications.
Key Features of Raspberry Pi 4
- Quad-core Cortex-A72 processor
- Up to 8GB of RAM
- Gigabit Ethernet port
- USB 3.0 ports
- Wi-Fi and Bluetooth connectivity
These features make the Raspberry Pi 4 a versatile device capable of handling demanding tasks such as running a firewall. Its compact size and low power consumption also make it an attractive option for home and small business networks.
Why Use Raspberry Pi as a Firewall?
Using a Raspberry Pi 4 as a firewall offers several advantages:
- Cost-Effective: The Raspberry Pi 4 is affordable compared to dedicated hardware firewalls.
- Customizable: You can tailor the firewall to meet your specific security needs.
- Open Source: Access to a wide range of open-source firewall software provides flexibility and control.
- Low Power Consumption: Ideal for environments where energy efficiency is a priority.
Whether you're a tech enthusiast or a small business owner, the Raspberry Pi 4 can serve as a reliable and efficient firewall solution.
Software Options for Raspberry Pi Firewall
Several software options are available for setting up a firewall on your Raspberry Pi 4. Some of the most popular choices include:
1. Pi-hole
Pi-hole is a network-wide ad blocker that can also function as a DNS-based firewall. It blocks unwanted ads and malicious domains, enhancing your network's security.
2. pfSense
pfSense is a powerful open-source firewall and router software that can be installed on the Raspberry Pi 4. It offers advanced features such as intrusion detection, load balancing, and traffic shaping.
3. OPNsense
OPNsense is another robust firewall solution that provides comprehensive security features. It supports various plugins and modules, allowing you to extend its functionality.
Choosing the right software depends on your specific requirements and technical expertise. Each option has its strengths, so it's essential to evaluate them based on your needs.
Step-by-Step Guide to Setting Up a Firewall
Here’s a step-by-step guide to help you set up your Raspberry Pi 4 as a firewall:
Step 1: Prepare Your Raspberry Pi
Before you begin, ensure your Raspberry Pi 4 is properly set up with the latest version of Raspberry Pi OS. Update the system by running the following commands:
sudo apt update and sudo apt upgrade.
Step 2: Install Firewall Software
Choose the firewall software that best suits your needs. For example, to install Pi-hole, use the following command:
curl -sSL https://install.pi-hole.net | bash.
Step 3: Configure Network Settings
Set up your Raspberry Pi 4 to act as a gateway between your internal network and the internet. This involves configuring the network interfaces and enabling IP forwarding.
Step 4: Test Your Setup
After completing the installation and configuration, test your firewall to ensure it's functioning correctly. Use tools like ping and traceroute to verify connectivity.
Following these steps will help you establish a secure and reliable firewall using your Raspberry Pi 4.
Network Configuration
Proper network configuration is critical for the effective operation of your Raspberry Pi 4 firewall. Below are some key considerations:
- Assign Static IP Addresses: Ensure your Raspberry Pi 4 has a static IP address to avoid conflicts.
- Enable IP Forwarding: Allow traffic to pass through your Raspberry Pi by enabling IP forwarding in the kernel.
- Set Up DHCP and DNS: Configure DHCP and DNS services to manage device connections and domain resolution.
By carefully configuring your network settings, you can optimize the performance and security of your Raspberry Pi firewall.
Advanced Security Settings
To further enhance the security of your Raspberry Pi 4 firewall, consider implementing the following advanced settings:
1. Intrusion Detection and Prevention
Use tools like Snort or Suricata to detect and prevent intrusions in real-time. These tools analyze network traffic and block suspicious activities.
2. Regular Updates and Patches
Keep your firewall software and operating system up to date with the latest security patches. Regular updates help protect against emerging threats.
3. Log Monitoring
Monitor firewall logs to identify potential security breaches and take corrective actions. Tools like Log2Ram can help reduce wear on your SD card by storing logs in RAM.
Implementing these advanced security measures will provide an additional layer of protection for your network.
Troubleshooting Tips
Even with careful planning, issues may arise during the setup process. Here are some troubleshooting tips:
- Check Network Connectivity: Ensure all devices are properly connected and configured.
- Verify Firewall Rules: Double-check your firewall rules to ensure they are correctly set up.
- Consult Documentation: Refer to the official documentation for your chosen firewall software for guidance.
By addressing common issues promptly, you can ensure your Raspberry Pi 4 firewall operates smoothly.
Additional Security Measures
For maximum security, consider implementing the following additional measures:
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to your Raspberry Pi by enabling 2FA.
- Limit SSH Access: Restrict SSH access to trusted IP addresses to prevent unauthorized access.
- Use Strong Passwords: Ensure all accounts on your Raspberry Pi use strong, unique passwords.
These measures will help safeguard your Raspberry Pi 4 firewall against potential threats.
Conclusion
In conclusion, setting up your Raspberry Pi 4 as a firewall is an excellent way to enhance your network's security. By following the steps outlined in this guide, you can create a robust firewall that meets your specific needs.
We encourage you to share your experience or ask questions in the comments section below. Additionally, feel free to explore other articles on our site for more tips and tricks on optimizing your Raspberry Pi setup. Together, let’s build a safer digital world!
Remember, cybersecurity is an ongoing process. Stay informed, stay vigilant, and keep your network secure.

How To Install And Manage The Raspberry Pi Firewall? Revised 2024
Firewall builder raspberry pi coverholden

StepbyStep Guide Configuring a Firewall on Raspberry Pi RaspberryTips